Day 9 - Unlocking the Secrets - My First Dive into Cryptography!
On this 9th day, I'm taking my first steps into the fascinating world of cryptography! Learning about secret messages, codes, and the science of keeping information safe.
Wow, what a journey this Cyber Bootcamp is! After getting hands-on with my lab and Linux, today, Day 9, we're stepping into a realm that's always fascinated me: Cryptography. It's the art and science of secret communication. When I hear "cryptography," I think of spy movies, encrypted emails, and secure websites. But it's so much more and, as I'm learning, it's woven into almost everything we do digitally. This book, Understanding Cryptography" by Christof Paar and Jan Pelzl, is going to be my guide.
Cryptography has been around for ages, not just in modern electronic communication. Think ancient Egypt with secret hieroglyphics or ancient Rome with the Caesar cipher. But today, my focus is on understanding the modern fundamentals.
Cryptology
The first thing I learned is that the umbrella term is Cryptology. It's not just about making codes; it's a whole field that splits into two main branches:
- Cryptography: This is the science of secret writing. The main goal here is to hide the meaning of a message.
- Cryptanalysis: This is the science (and sometimes art!) of breaking those secret systems. It might sound like something only intelligence agencies do, but a lot of cryptanalysis is actually done by academic researchers. Why? Because without people trying to break crypto methods, we'd never know if they're truly secure!
This book will mainly focus on cryptography, showing me how practical crypto algorithms work – the ones that have stood up to a lot of cryptanalysis.
The Main Flavors of Cryptography
Cryptography itself has a few main areas:
- Symmetric Algorithms: This is the classic idea of secret codes. Two parties (let's call them Alice and Bob, as is tradition!) share a secret key to encrypt and decrypt messages. All cryptography from ancient times until 1976 was based on these symmetric methods, and they're still super important today for things like data encryption.
- Asymmetric (or Public-Key) Algorithms: This is a newer concept, introduced in 1976, where a user has both a public key and a private key.
- Cryptographic Protocols: These are like the recipes that use cryptographic algorithms as ingredients. They define how to apply these algorithms to build secure applications, like the TLS (Transport Layer Security) that secures web browse.
Often, systems use a mix of symmetric and asymmetric algorithms (and another tool called hash functions, which I'll learn about later) – these are called hybrid schemes. Each type has its own strengths and weaknesses.

Asymmetric Cryptography: The Two-Key System
Before we dive deep into the older symmetric systems, I want to expand a little on Asymmetric Cryptography because it's such a game-changer. As I mentioned, this was introduced in 1976 by Whitfield Diffie, Martin Hellman, and Ralph Merkle. The core idea is that a user possesses a secret key (sometimes called a private key) just like in symmetric cryptography, but they also have a public key. This public key can be shared with anyone without compromising security.
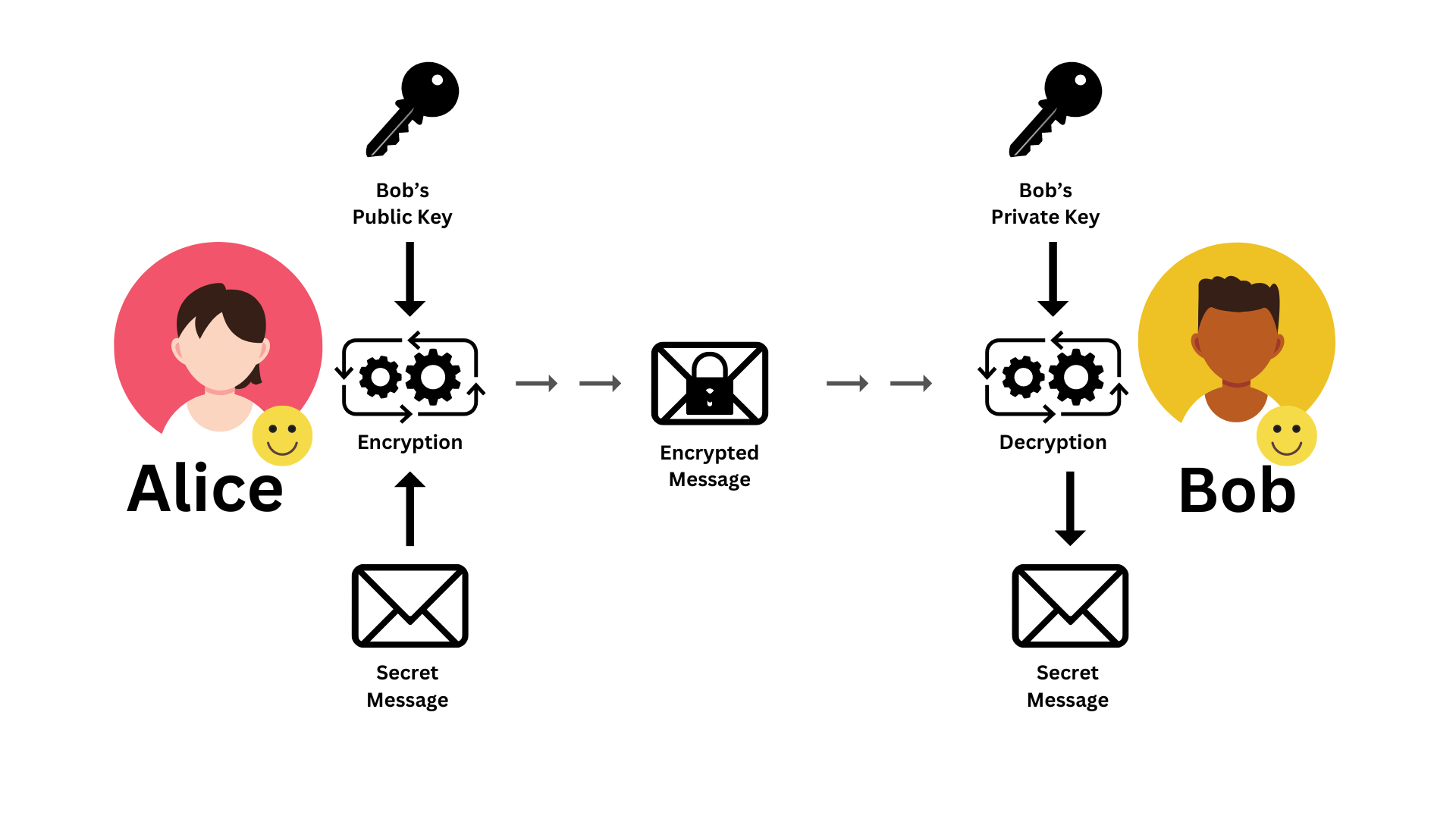
This two-key system allows for some amazing capabilities that symmetric systems struggle with:
- Digital Signatures: Proving that a message really came from a specific person and hasn't been tampered with.
- Key Establishment: Securely creating shared secret keys over an insecure channel, which is a major hurdle for symmetric systems.
- Classical Data Encryption: Yes, it can also be used for encrypting data, but often it's used in conjunction with symmetric ciphers for this due to performance reasons.
It's a very different way of thinking about secrets, and I'm keen to learn more about the specific algorithms like RSA later on!
Symmetric Cryptography: The Basics
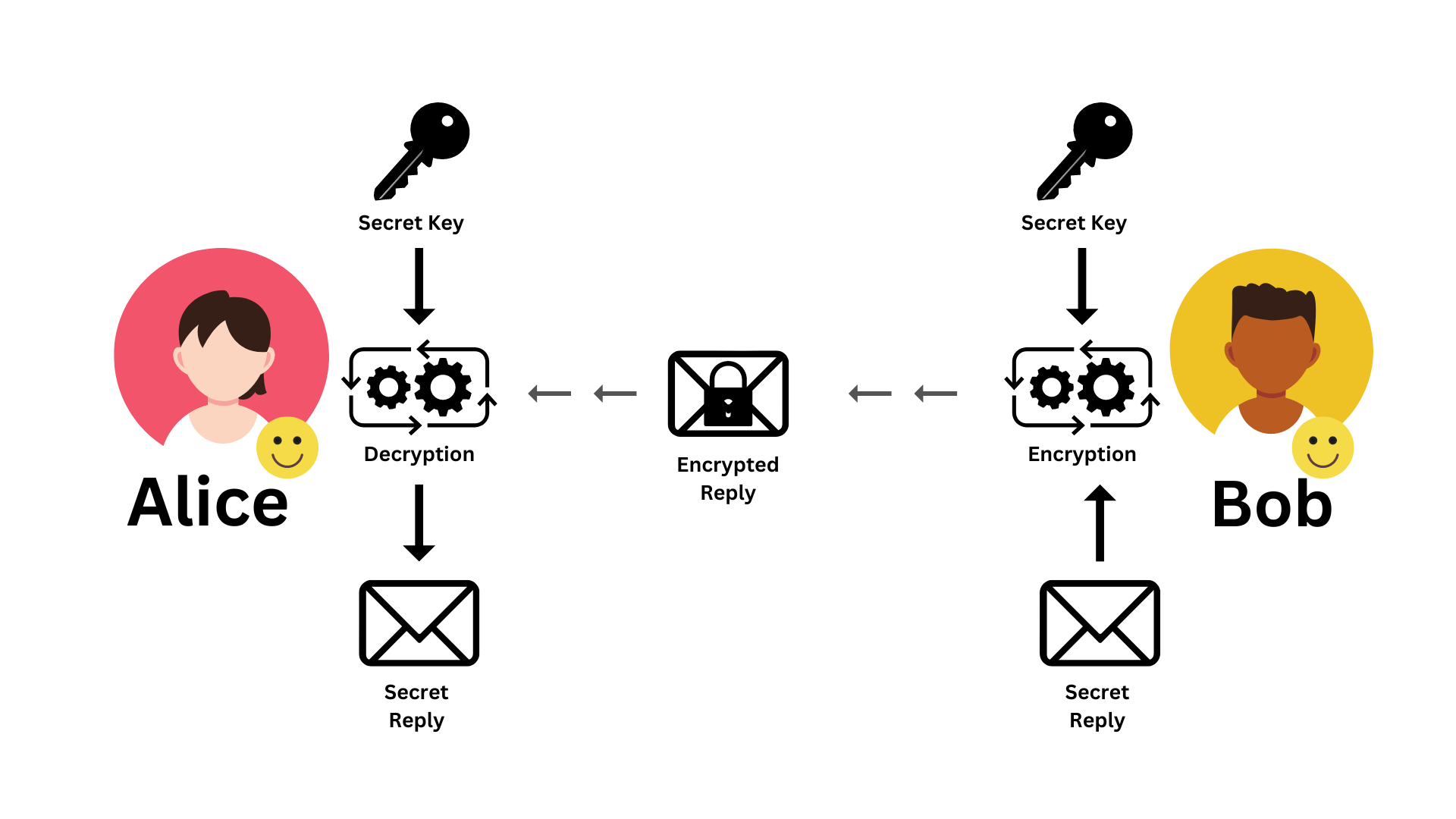
Let's zoom in on symmetric cryptography. Imagine Alice wants to send a secret message to Bob over an insecure channel (like the internet, where a "bad guy," often called Oscar, might be listening or eavesdropping).
- Plaintext (x): This is Alice's original, readable message.
- Encryption (e()): Alice uses an encryption algorithm and a secret key (k) to transform her plaintext into a jumbled, unreadable message.
- Ciphertext (y): This is the encrypted, unreadable message that travels over the insecure channel. To Oscar, if the encryption is strong, this should look like random nonsense.
- Decryption (d()): Bob receives the ciphertext and uses the same secret key (k) and a decryption algorithm (which is usually the inverse of encryption) to turn the ciphertext back into the original plaintext.
The big challenge here is how Alice and Bob get that shared secret key in the first place. They need a secure channel for that initial key distribution. Once they have the key, they can use it for many messages.
A really important idea here is Kerckhoffs' Principle, formulated way back in 1883. It states:
A cryptosystem should be secure even if the attacker (Oscar) knows all details about the system, with the exception of the secret key.
This means the encryption and decryption algorithms themselves should be publicly known. It sounds counterintuitive – wouldn't keeping the algorithm secret make it safer? But experience shows that "security by obscurity" is a bad idea. Secret algorithms don't get tested by the wider community of cryptographers, so their weaknesses might never be found until it's too late. The only thing that should be secret is the key.
A Classic Example: The Substitution Cipher
To make things concrete, I looked at a very old and simple symmetric cipher: the Substitution Cipher. The idea is basic: you substitute each letter of the alphabet with another one. For example, if 'A' becomes 'k', 'B' becomes 'd', and so on, then "ABBA" would encrypt to "kddk". The key for this cipher is the substitution table itself – the mapping of which letter becomes which. Alice and Bob would need to share this table securely beforehand.
Now, how would Oscar try to break this?
- Brute-Force Attack (Exhaustive Key Search): If Oscar has a piece of ciphertext and maybe a tiny bit of corresponding plaintext (like a common file header), he could try decrypting the ciphertext with every single possible key (every possible substitution table) until he finds a match. For the English alphabet, the number of possible keys (the key space) is 26! (26 factorial), which is about 288. That's a huge number! Even with powerful computers, trying all those keys would take decades. So, the substitution cipher seems secure, right? Wrong! Because there is more powerful attack.
- Analytical Attack (Letter Frequency Analysis): This is where understanding the cipher's structure helps. The substitution cipher's main weakness is that each plaintext letter always maps to the same ciphertext letter. This means statistical properties of the plaintext language are preserved in the ciphertext. For instance, in English, 'E' is the most frequent letter (about 13%), followed by 'T' (9%), then 'A' (8%). If Oscar sees a ciphertext where the letter 'q' appears most often, he can guess that 'q' probably represents 'E'. By analyzing frequencies of single letters, pairs (like 'Q' almost always followed by 'U'), and common short words, the substitution cipher can be broken relatively easily, even with its large key space.

The lesson here? A large key space alone isn't enough! Good ciphers need to hide the statistical properties of the plaintext, making the ciphertext appear random.
Key Length: How Many Bits Protect Your Secrets?
This brings me to key length. For symmetric ciphers, if a brute-force attack is the best known way to break it, the key length is critical. The more possible keys, the longer a brute-force attack will take. I also learned that key lengths for symmetric ciphers (like AES) and asymmetric ciphers (like RSA) are dramatically different to offer similar security. For example, an 80-bit symmetric key might offer similar security to a 1024-bit RSA key. For modern symmetric ciphers, key lengths like 128 bits or 256 bits are considered very strong and should protect data for decades, even against very determined attackers.
Phew, that was a lot for an introduction! Cryptography is a deep and complex field, but even these initial concepts are incredibly interesting. It's clear that designing secure systems requires careful thought about not just the algorithms, but how they're used and the potential ways attackers might try to break them. Can't wait to learn more!
#IDNBootCampCyber


Komentar
Posting Komentar